Lesson 34: Malicious Contracts & Scam Token Surveillance (Protecting Your Users from Social Engineering)
Not every threat is a technical exploit. Sometimes, the weapon is social engineering, and the payload is a smart contract.
In this lesson, we will get into malicious contract deployments, scam tokens, and deceptive airdrops before they harm users.
Why This is important in Blockchain Monitoring
Even if a contract isn’t vulnerable in code, it may be malicious by intent.
As a Forta bot developer, you can:
Identify tokens with malicious behaviors
Identify newly deployed contracts that exhibit scam-like behavior.
Spot malicious airdrops designed to trick unsuspecting users.
Detect unusual patterns in token approvals or transfers that may indicate fraud.
These detections help frontends, wallets, and explorers to warn users before they interact with the trap.
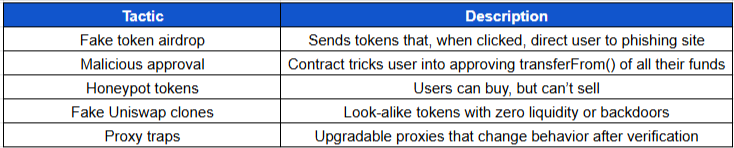
Common Scam Tactics
How to Detect Scam Contracts
1. Unverified Contracts
Contract is deployed
But source code is not verified
You can flag this immediately via:
No matching source on Etherscan
No proxy implementation verified
2. Suspicious Constructor Patterns
Owner set to EOA instead of multisig
Large initial mint to a single wallet
Approvals to unknown addresses
3. Fake Airdrop Patterns
Sends tiny amounts to random wallets
Includes token name like “Claim Now” or “Free NFT”
Links in token metadata or transfer memo
Forta Agent Examples
Basic Unverified Contract Alert
async function handleTransaction(txEvent) {
const findings = [];
for (const contract of txEvent.contractsCreated) {
if (!await isVerified(contract)) {
findings.push(
Finding.fromObject({
name: "Unverified Contract",
description: `New contract deployed at ${contract} with no source code`,
alertId: "UNVERIFIED-CONTRACT",
severity: FindingSeverity.Medium,
type: FindingType.Suspicious,
})
);
}
}
return findings;
}
You can build isVerified() using Etherscan API check.
Token Pattern Detection
Flag tokens with:
transfer()reverting for certain addressesapprove()immediately followed bytransferFrom()by attackerLarge mint followed by liquidity pool creation
Key Concepts Recap
Not all threats are code bugs, many are malicious behaviors
Monitoring for scam tokens protects users before interaction
Forta can flag unverified contracts, shady tokens, and social engineering traps
You act as the guardian of the innocent, shielding them from deception
Next lesson we will explore MEV & Front-Running Bots, detecting exploitation in the mempool.
🙏 Until next meditation,
The Blockchain Security Monk