Lesson 35: MEV & Front-Running Bots (Detecting Exploitation in the Mempool)
Bots compete in the mempool to extract value from pending transactions before they’re confirmed. This process, known as MEV (Maximal Extractable Value) and front-running, allows them to legally profit at the expense of users and protocols.
Today, we will explore how Forta bots can spot these attacks in real time, and how to build detection logic for various forms of MEV exploitation.
Why This is important in Blockchain Monitoring
MEV is a multi-billion dollar phenomenon, and some of its forms include:
Sandwich attacks on DEX swaps
Executing a transaction immediately after a liquidation to capture profit opportunities
Sending transactions with high gas fees to be first in line for limited NFT drops
Frontrunning governance proposals or bridge transactions
As a Forta Admin, your job is to monitor for these behaviors and alert teams, so they can protect users or add defenses.
What Is MEV?
MEV = the extra value a miner (or validator) can extract by reordering, inserting, or censoring transactions in a block.
Today, most MEV is captured by bots (searchers) that send bundles to block builders or validators.
Example: a Sandwich Attack
You send a DEX trade (e.g. 1000 USDC --> ETH)
MEV bot sees it in the mempool
It front-runs with a buy to move price up
Your trade goes through at worse price
It sells immediately after you for profit
You lose, they win.
How to Detect Sandwiches
You need to monitor:
3 consecutive transactions:
Token “A” buy
Large Token “A” swap (victim)
Token “A” sell
All 3 from same bot cluster or closely timed
Profitable price movement in attacker’s favor
Forta Bot Logic Outline
async function handleBlock(blockEvent) {
const findings = [];
const txs = blockEvent.transactions;
for (let i = 0; i < txs.length - 2; i++) {
const txA = txs[i];
const txB = txs[i+1];
const txC = txs[i+2];
if (isBuy(txA) && isLargeSwap(txB) && isSell(txC)) {
if (txA.from === txC.from) {
findings.push(
Finding.fromObject({
name: "Possible Sandwich Attack",
description: `Detected front-run and back-run around large swap`,
alertId: "MEV-SANDWICH",
severity: FindingSeverity.Medium,
type: FindingType.Exploit,
})
);
}
}
}
return findings;
}
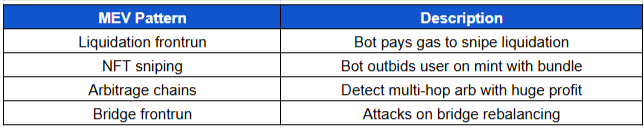
Alternative MEV Types You Can Detect
Challenges
Detecting MEV is tricky because:
It happens fast
Bundled txs via Flashbots aren’t always visible
Requires deep mempool and block analysis
Patterns evolve constantly
But Forta lets you embed logic in scan nodes, so you can still catch confirmed txs that match MEV shapes.
Example Project
Key Concepts Recap
MEV is invisible extraction of value by tx reordering and injection
Sandwich attacks are the most common type of MEV and detectable with Forta
Other forms like liquidation or NFT sniping can also be traced
Your bot is the lens to uncover these hidden exploiters
Next Lesson 36 we will get into the final exercise: Building a Full Security Monitoring Stack from Scratch.
🙏 Until next meditation,
The Blockchain Security Monk