Lesson 7: Routing Forta Alerts to Slack, Telegram and Incident Alerting tools
Today’s lesson teaches you how to route alerts generated by your Forta agents into real-time systems, so your team can react before your protocol is reduced to ashes by an exploit.
We will cover how to:
Connect Forta to Slack, Telegram, or PagerDuty
Use Webhooks and Alert APIs
Build an automated monitoring pipeline
What Is Alert Routing?
Every Forta agent emits Alerts when suspicious behavior is detected.
These alerts:
Are signed by the bot’s key
Are published to Forta’s global alert feed
Contain metadata about the detection
But alerts alone are passive. To become useful, you must forward them to:
Your incident response team
A community Discord/Telegram channel
Your internal SIEM tools
Dashboards, pagers, SMS systems
This process is called alert routing.
How Alert Routing Works – Step by Step
This is how alerts travel from the blockchain to your messaging apps:
A Forta agent emits an alert (via
Finding.fromObject(...))The alert is published by the scan node to the Forta network
You (or a third-party system) read the alert via:
Forta Explorer (GUI)
Forta Public API
Webhook Alert Feed
You push the alert to Slack, Telegram, email, or your own backend
Option 1: Use Forta Explorer's UI (No Code)
Ideal for small teams or early-stage protocols.
Go to Forta Explorer
Search your bot or contract address
Click "Subscribe to Alerts"
Choose your delivery method:
Slack (via Zapier or custom webhook)
Telegram
Email
Simple. Limited customization. Good for testing.
Option 2: Use the Forta Public API
If you want to integrate with your backend, write a bot, or automate response flows then use the Forta Alert API.
Basic Example:
curl -X POST https://api.forta.network/graphql \
-H "Content-Type: application/json" \
-d '{"query": "{ alerts(first: 5, botIds: [\"0xYourBotId\"], severities: [\"HIGH\"]) { alerts { alertId description metadata } } }"}'
You can then parse the response in:
Node.js
Python (using
requests)Zapier/Make HTTP step
Option 3: Create Your Own Webhook Listener
This is the most flexible approach. You write a server that listens for alerts, parses them, and pushes them forward.
Example: Node.js Webhook Server
const express = require("express");
const app = express();
app.use(express.json());
app.post("/forta-alert", (req, res) => {
const alert = req.body;
if (alert.alertId === "HIGH-ETH-TRANSFER") {
sendToSlack(alert);
}
res.sendStatus(200);
});
function sendToSlack(alert) {
const payload = {
text: ` Alert: ${alert.description}`,
attachments: [
{
fields: [
{ title: "Severity", value: alert.severity, short: true },
{ title: "Tx Hash", value: alert.metadata.txHash, short: true }
]
}
]
};
// POST to your Slack webhook URL
}
app.listen(3000, () => console.log("Alert listener running"));
Now connect your Forta scan node to POST alerts to this server.
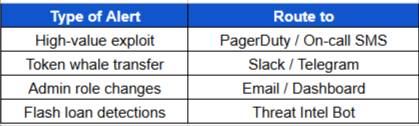
What to Route Where?
This is the critical connection between detecting a threat (via your Forta bot) and responding to it in real time (e.g. notifying your team, triggering an incident alert, updating dashboards, or executing an automated action)
Key Concepts Recap
Security doesn’t end at detection. It begins there.
Your real job is incident response, to take action when the bots notify you that “something is wrong.”
Forta becomes actionable only when alerts reach human systems. If that connection breaks, critical threats may be missed.
In the next lesson, we will explore the world of threat intelligence feeds, and how Forta’s public alerts become a global immune system for DeFi.
Until next meditation,
The Blockchain Security Monk